Attack Force Graph
Side Quest
2021
Generate JSON force-directed/ node graph data from MITRE’s ATTACK framework and visualize it interactively.
About
- Project I wanted to do as soon as I learned about force-directed graphs and the MITRE ATT&CK data seemed like a great candidate.
- Second goal was to brush up on creating unique elements in preparation for a project I worked on during my 2021 internship.
- Frontend was done without React/ other JS frameworks given how small the project is.
- Python script generates a
node->linkconnection.
Demo
View Demo (GitHub Pages)
Preview
What?
-
Generate JSON force-graph data nodes and links from the MITRE ATTACK Framework based on your preferences. (
graph_generator.py) -
Use that data to visualize your results with a UI tailored around the ATTACK data. (
frontenddirectory) -
The JSON data generated is formatted for use with @vasturiano’s awesome various force-directed graph projects. (Tested and works on both 2D and 3D versions)
-
At the moment you can do the following combinations:
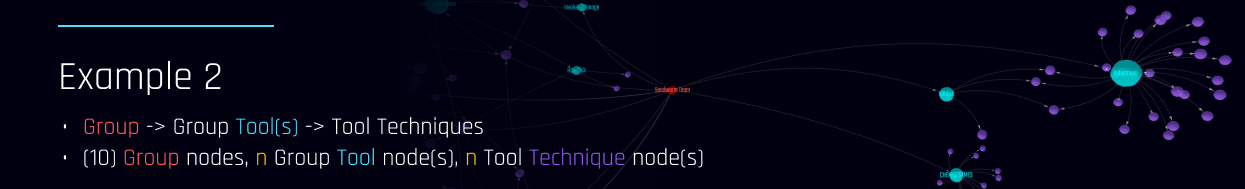
- Group -> Group Tools -> Group Tool Techniques:
- Each group (APT) node will be linked to the corresponding tools/ software the group uses.
- Total node connections: (group * n group tools * n tool techniques)
- Group -> Group Tools/ Software:
- Links just the tools without fetching tool techniques data
- Total node connections: (group * n group tools)
- Groups Only
- A node for each group will be generated but no links. (What would you link a group to?!)
- Total node connections: 0
- Other
- You can generate standalone nodes of groups or group tools/ software.
- Group -> Group Tools -> Group Tool Techniques:
Why?
- Draw conclusions and spot patterns fast thanks to the power of data visualization.
- Present compelling data stakeholders can easily understand and interact with.
- Force-directed graphs are seriously… 😎 cool
How?
- The graph generator script uses @Cyb3rWard0g’s ATTACK-Python-Client to build the ATTACK graph data. Having used MITRE’s STIX… I definitely recommend using Roberto’s package.
- Lift requests are network requests and can be time-consuming. Efficiency improvements planned after the main portion is done.
- The 3D graph in the UI is the 3D version of vasturiano’s awesome JS force-directed graphs.
Example Demos:
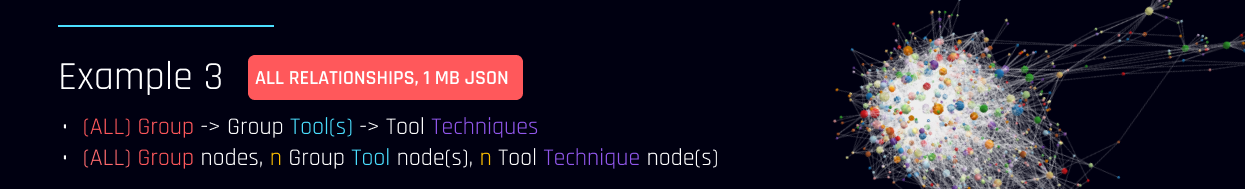
Full ATTACK data demo with UI
- Graphs Only:
Examples:
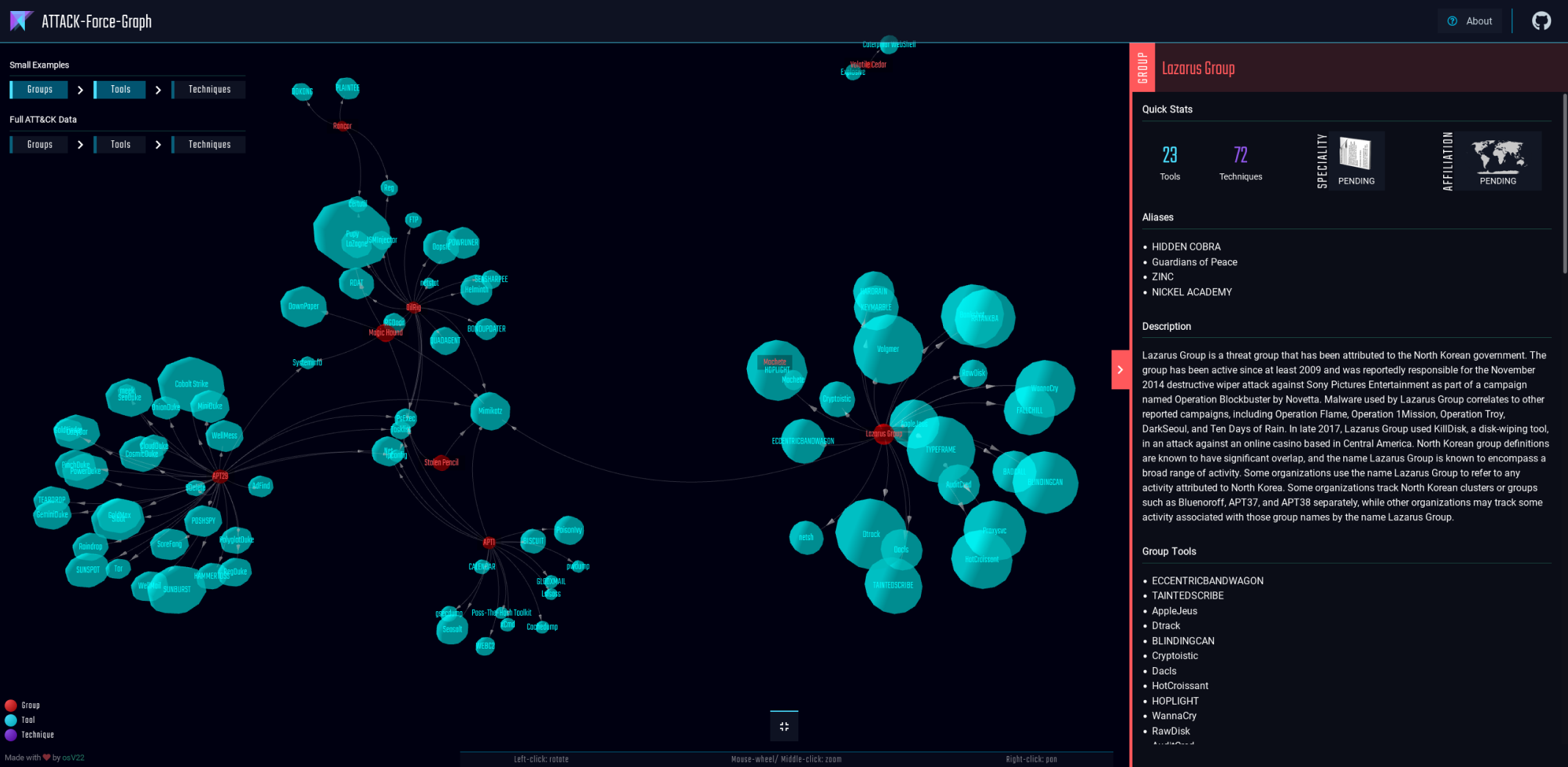
Data Preview:
-
NOTE: Specific values are not part of the MITRE ATTACK Framework:
- Group:
affiliation- This is subjective and can be problematic, so it is up to your assessment to evaluate which group is affiliated with whom. - Group:
targets- Work-in-progress for defaults but hard to maintain over time given that it is not part of the ATTACK framework. - Group:
speciality- Work-in-progress and is much easier to maintain.
- Group:
-
val- This can be used to determine how big you want a node element to be.- For groups: The
valis based on the number of tools the group uses - For tools: The
valis based on the number of techniques the tool makes possible - For techniques: Set to
Noneby default, leaving it up to you
- For groups: The
Group Node
1{
2 "id": "MITRE GROUP ID HERE. EX: G0005",
3 "type": "group",
4 "val": 2,
5 "attributes": {
6 "name": "Cool Group/ APT Name Here",
7 "aliases": [
8 "Group alias",
9 "Operation Golden Kitty"
10 ],
11 "description": "Cleaned description. Do not use `get_desc()` if you want raw desc...",
12 "affiliation": "You have to assign this value yourself, read the NOTE above :)",
13 "targets": ["Also you have to", "set this. Read NOTE above"],
14 "speciality": ["set this based on your assessment", "Read NOTE above"],
15 "tools": {
16 "tool_id_here": "tool_name_here",
17 "S0225": "sqlmap",
18 },
19 "techniques": {
20 "technique_id_here": "technique_name_here",
21 "T1566.003": "Spearphishing via Service",
22 }
23 }
24}
Tool Node
1{
2 "id": "MITRE Software ID HERE. EX: S0084",
3 "type": "tool",
4 "val": 1
5 "attributes": {
6 "name": "tool_name_here",
7 "aliases": [],
8 "labels": [
9 "tool"
10 ],
11 "description": "Cleaned description. Do not use `get_desc()` if you want raw desc..",
12 "platforms": [
13 "Linux",
14 "Windows"
15 ],
16 "techniques": {
17 "T1190": "Exploit Public-Facing Application"
18 }
19 }
20}
Technique Node
valis set toNoneby default, you can set it to length of platforms or whatever your preference is.
1{
2 "id": "MITRE Technique ID HERE. EX: T1190",
3 "type": "technique",
4 "val": null,
5 "attributes": {
6 "name": "Exploit Public-Facing Application",
7 "chain_phase": "initial-access",
8 "description": "Cleaned description. Do not use `get_desc()` if you want raw desc.",
9 "detection": "Cleaned detection. Do not use `get_desc()` if you want raw detection paragraph...",
10 "is_subtype": false,
11 "platforms": [
12 "Windows"
13 ]
14 }
15}